What is Monitoring Proxy? Its Contribution to Monitoring Processes
In monitoring systems, especially in large and distributed infrastructures, sending all monitoring data directly to a central server can be inefficient. This is where a monitoring proxy comes into play. A proxy in monitoring is a server that acts as an intermediary between a monitoring agent and the device or application being monitored. Its primary goal is to lighten the load on the monitoring system, optimize network traffic, and enable the monitoring of devices in remote or isolated networks.
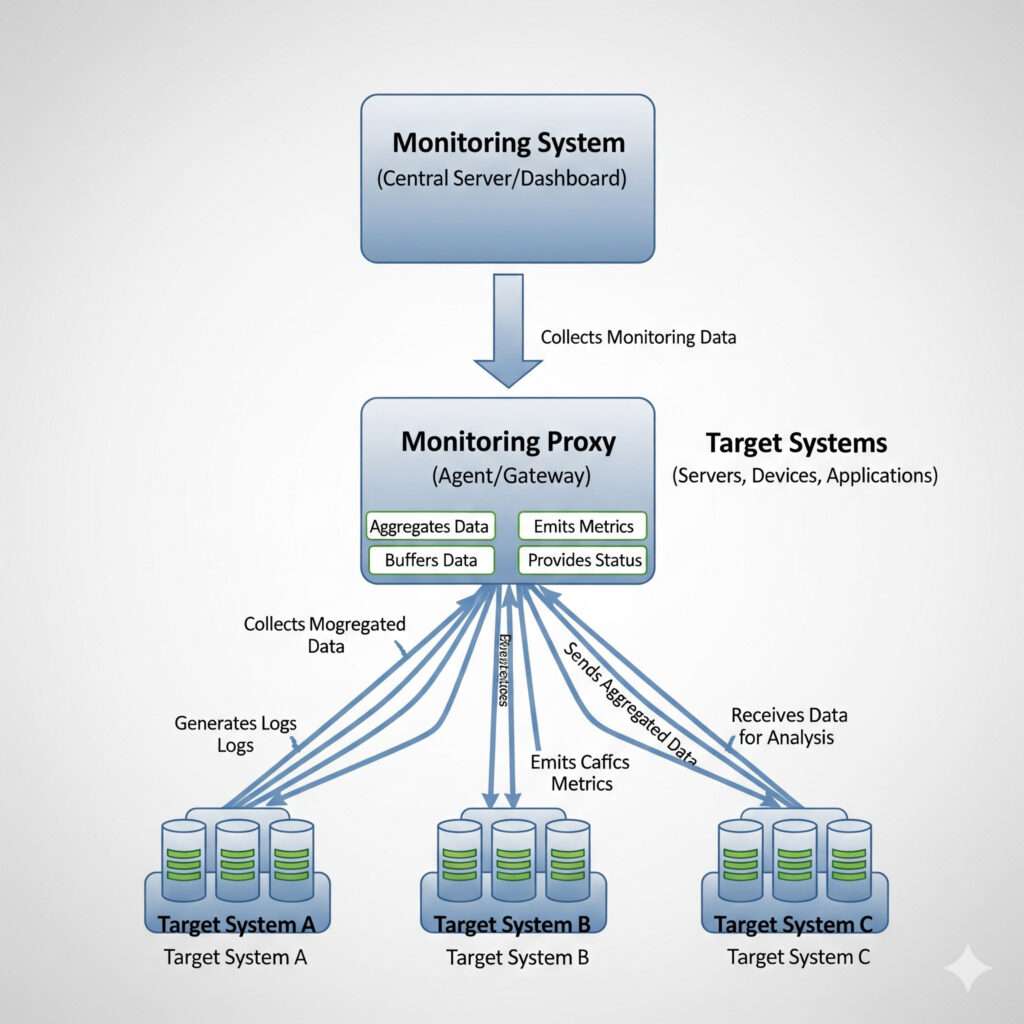
What Is a Monitoring Proxy?
A monitoring proxy is a middleman that bridges your monitoring system (e.g., Zabbix, Prometheus) and the devices you are monitoring. Instead of sending data directly to the central server, devices first send their data to the proxy server. The proxy receives, processes (by compressing or filtering), and then forwards this data in bulk to the main monitoring server. This makes the monitoring process much more efficient and secure.
How Does a Proxy Work?
The operational logic of a proxy is as follows:
- Data Collection: The proxy collects metrics and log data from monitored devices (servers, network devices, applications, etc.). This data can include performance indicators like CPU usage, memory, disk space, and network traffic.
- Preprocessing: Before being sent to the main monitoring server, the collected data can be filtered, compressed, or grouped on the proxy itself. This reduces network traffic and lightens the load on the central server.
- Transmission: The proxy securely and efficiently transmits the processed data to the main monitoring server. The central server then receives, analyzes, and visualizes this data on a dashboard or through a reporting tool.
Why Use a Proxy? Goals and Advantages
Reduced Network Traffic & Optimization
Collecting data from devices in remote locations can be problematic with slow or costly network connections. A proxy minimizes network traffic by compressing or sending data in batches.
Secure Data Collection
The monitored devices do not need direct access to the main monitoring server. This reduces security risks, especially when monitoring devices in different network segments or behind firewalls. All data traffic is managed through a single proxy.
Easing the Central Server's Load
A high volume of devices constantly sending data can exhaust a central server; a proxy balances this load.
Offline Operation Capability
If the main monitoring server becomes unreachable, proxies can cache data locally and continue sending it once the central server is back online. This prevents data loss.
Scalability
In large-scale infrastructures, monitoring hundreds or thousands of devices simultaneously can severely impact the performance of the main server. Proxies distribute this load, easing the main server’s workload and enabling your system to easily monitor more devices. Each proxy manages the devices in its region and sends consolidated data to the main server.
Security
One of the most significant benefits is security. Devices in different network segments or behind firewalls do not need direct access to the central monitoring server. All communication happens through one secure point, the proxy, which significantly reduces your network’s attack surface.
Fault Tolerance and High Availability
If your main monitoring server temporarily goes offline due to an issue, the proxy caches data locally. When the main server comes back online, the proxy automatically sends the accumulated data. This prevents data loss and ensures monitoring continuity.
Common Monitoring Proxy Use Cases
Multi-Branch Businesses
This is ideal for companies with branches in different geographical locations. You can install a proxy at each branch to centrally manage local networks.
Cloud and Hybrid Environments
Businesses with both on-premise and cloud-based (AWS, Azure, GCP) infrastructures can install separate proxies for each environment to simplify their monitoring processes.
Isolated or Security-Focused Networks
It is the most secure way to monitor devices in networks with restricted internet access or strict security rules.
In conclusion, using a monitoring proxy is the key to making your IT infrastructure’s monitoring architecture more secure, efficient, and scalable. Whether you are a small or large business, investing in this technology is one of the most important steps you can take to maintain the health of your systems and proactively resolve potential issues.
Fill the Form, We’ll Reach Out!


