Perimeter Security and Intrusion Detection
AI-powered perimeter security and intrusion detection transform your existing cameras into intelligent devices, providing around-the-clock active protection for your monitored premises!

What is Perimeter Security and Intrusion Detection?
Perimeter security and intrusion detection is an intelligent security solution that monitors facility boundaries 24/7, instantly detecting unauthorized objects such as people or vehicles entering critical areas. This system analyzes video feeds from existing CCTV cameras using AI algorithms, filtering out irrelevant triggers like tree movements or lighting changes and focusing solely on genuine threats.
By identifying small, fast, or unusual movements that might be missed by the human eye, it reduces the workload on security personnel and enables faster, more accurate incident response. As a result, perimeter security becomes more proactive, data-driven, and highly accurate.

Perimeter security and intrusion detection is an intelligent security solution that monitors facility boundaries 24/7, instantly detecting unauthorized objects such as people or vehicles entering critical areas. This system analyzes video feeds from existing CCTV cameras using AI algorithms, filtering out irrelevant triggers like tree movements or lighting changes and focusing solely on genuine threats.

By identifying small, fast, or unusual movements that might be missed by the human eye, it reduces the workload on security personnel and enables faster, more accurate incident response. As a result, perimeter security becomes more proactive, data-driven, and highly accurate.

Perimeter security and intrusion detection is an intelligent security solution that monitors facility boundaries 24/7, instantly detecting unauthorized objects such as people or vehicles entering critical areas. This system analyzes video feeds from existing CCTV cameras using AI algorithms, filtering out irrelevant triggers like tree movements or lighting changes and focusing solely on genuine threats.
By identifying small, fast, or unusual movements that might be missed by the human eye, it reduces the workload on security personnel and enables faster, more accurate incident response. As a result, perimeter security becomes more proactive, data-driven, and highly accurate.
How Does Intrusion Detection Work?
The Intrusion Detection Algorithm (Intrusion Agent) operating within the IRIS+ platform employs deep learning-based artificial neural networks to accurately detect, in real time, unauthorized entries of objects such as people or vehicles into critical areas within the perimeter. It is capable of identifying very small targets, even those measuring only a few pixels in size.
The Intrusion Detection Algorithm (Intrusion Agent) operating within the IRIS+ platform employs deep learning-based artificial neural networks to accurately detect, in real time, unauthorized entries of objects such as people or vehicles into critical areas within the perimeter. It is capable of identifying very small targets, even those measuring only a few pixels in size.
AI-Powered Advanced Filtering to Minimize False Alarms
Leveraging deep learning techniques, the algorithm reliably distinguishes between humans and vehicles. It also detects and filters out non-critical movements—such as swaying leaves or raindrops—effectively neutralizing them. This allows security operators to focus exclusively on genuine threats. By differentiating insignificant motions like tree leaves or clouds, the system significantly reduces the false alarm rate.
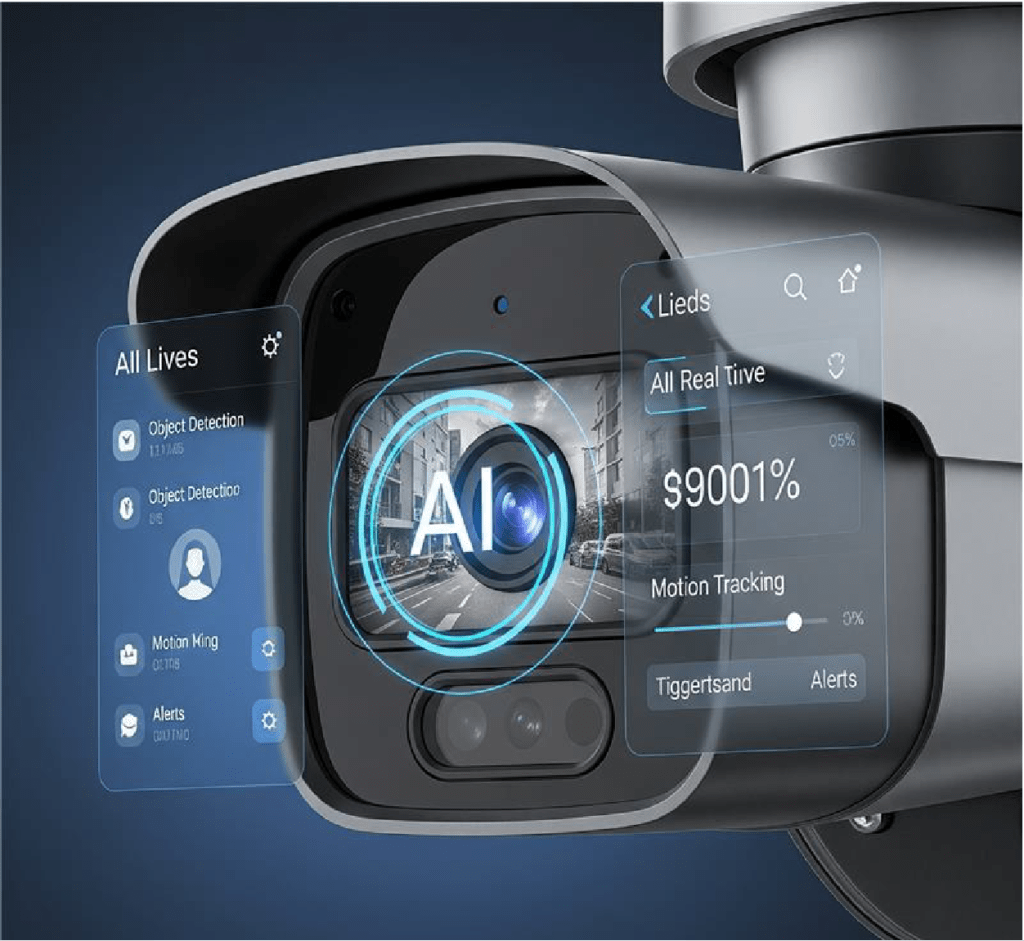
Leveraging deep learning techniques, the algorithm reliably distinguishes between humans and vehicles. It also detects and filters out non-critical movements—such as swaying leaves or raindrops—effectively neutralizing them. This allows security operators to focus exclusively on genuine threats. By differentiating insignificant motions like tree leaves or clouds, the system significantly reduces the false alarm rate.


Leveraging deep learning techniques, the algorithm reliably distinguishes between humans and vehicles. It also detects and filters out non-critical movements—such as swaying leaves or raindrops—effectively neutralizing them. This allows security operators to focus exclusively on genuine threats. By differentiating insignificant motions like tree leaves or clouds, the system significantly reduces the false alarm rate.
Benefits of Perimeter Security and Intrusion Detection
Intrusion detection instantly identifies and alarms unauthorized individuals or vehicles entering designated areas—such as forklift traffic corridors, hazardous chemical or flammable material storage, loading docks, production machinery zones, high-voltage lines, and technical rooms housing maintenance equipment. This allows security teams to intervene before or at the very early stages of an incident, preventing damages caused by delayed detection and ensuring perimeter security.
In critical sites like industrial facilities, energy infrastructures, or data centers, unauthorized access poses not only perimeter security risks but also operational disruption threats. By digitizing environmental security in these areas, the system helps prevent serious losses such as production downtime, data breaches, or workplace accidents.
Unauthorized entry is a significant threat not only to perimeter security but also to occupational health and safety. Immediate detection of unauthorized individuals in hazardous or restricted zones enhances employee safety and ensures compliance with legal obligations, enabling organizations to proactively fulfill their responsibilities.
Operational Scope and Use Case Portfolio

Fences, walls, and boundary areas surrounding factories and industrial facilities are frequent targets for unauthorized access. AI-powered intrusion detection instantly identifies physical breaches such as fence climbing, tunneling, or cutting. Especially during nighttime hours when human observation is limited, the system automatically detects such attempts, minimizing security vulnerabilities.
Loading docks and warehouse entry points are critical security zones due to high vehicle and foot traffic. Intrusion Detection monitors these areas in real time to prevent unauthorized personnel from entering shipping zones. While safeguarding valuable goods during loading and unloading, it also detects unauthorized access outside shift hours, helping prevent losses such as stock theft.
Due to their expansive, open layouts, continuous human monitoring of open storage areas and construction sites is challenging. Intrusion Detection provides early warning against theft of materials and equipment by automatically detecting unauthorized entries, especially during off-hours. The system promptly alerts security teams to prevent undetected infiltration by unattended vehicles or individuals.

Fences, walls, and boundary areas surrounding factories and industrial facilities are frequent targets for unauthorized access. AI-powered intrusion detection instantly identifies physical breaches such as fence climbing, tunneling, or cutting. Especially during nighttime hours when human observation is limited, the system automatically detects such attempts, minimizing security vulnerabilities.

Loading docks and warehouse entry points are critical security zones due to high vehicle and foot traffic. Intrusion Detection monitors these areas in real time to prevent unauthorized personnel from entering shipping zones. While safeguarding valuable goods during loading and unloading, it also detects unauthorized access outside shift hours, helping prevent losses such as stock theft.

Due to their expansive, open layouts, continuous human monitoring of open storage areas and construction sites is challenging. Intrusion Detection provides early warning against theft of materials and equipment by automatically detecting unauthorized entries, especially during off-hours. The system promptly alerts security teams to prevent undetected infiltration by unattended vehicles or individuals.

Some facilities contain restricted zones accessible only to authorized personnel that involve risks such as high heat, chemicals, or moving machinery. AI-assisted intrusion detection immediately identifies unauthorized access to these areas, safeguarding employee occupational health and safety while maintaining operational integrity. This reduces potential workplace accidents and associated legal risks.

Research and development and sensitive production areas are critical zones where new products are designed, existing technologies improved, and innovation pursued. Due to the presence of confidential information, prototypes, and advanced technology components, these areas pose high risks both for information and physical security. Intrusion Detection instantly flags unauthorized access, protecting intellectual property, ensuring data security, and guaranteeing production continuity.

Access to certain critical zones is allowed only during specified times and requires identity verification. AI-enabled video analytics systems detect and alert on any entry attempts outside authorized hours. They can identify unauthorized passage among employees and automatically monitor visitor movements. As part of perimeter security protocols, all after-hours access attempts are instantly detected and operators notified.

Some facilities contain restricted zones accessible only to authorized personnel that involve risks such as high heat, chemicals, or moving machinery. AI-assisted intrusion detection immediately identifies unauthorized access to these areas, safeguarding employee occupational health and safety while maintaining operational integrity. This reduces potential workplace accidents and associated legal risks.

Research and development and sensitive production areas are critical zones where new products are designed, existing technologies improved, and innovation pursued. Due to the presence of confidential information, prototypes, and advanced technology components, these areas pose high risks both for information and physical security. Intrusion Detection instantly flags unauthorized access, protecting intellectual property, ensuring data security, and guaranteeing production continuity.

Access to certain critical zones is allowed only during specified times and requires identity verification. AI-enabled video analytics systems detect and alert on any entry attempts outside authorized hours. They can identify unauthorized passage among employees and automatically monitor visitor movements. As part of perimeter security protocols, all after-hours access attempts are instantly detected and operators notified.
In employee parking lots and service vehicle zones, the system detects individuals concealed among vehicles and instantly alerts operators of any potential unauthorized access. Additionally, it generates automatic warnings against unauthorized vehicle use, off-service entries or exits, and attempts involving stolen vehicles, thereby reinforcing perimeter security.
Interested in Perimeter Security and Intrusion Detection? Fill the Form, We’ll Reach Out!


