
What Should Be Done for PCI DSS Regulation?
Recent data breaches, hacking incidents that resulted in massive money losses, and scant reports of cybersecurity have begun to distrust customers of payment and money institutions. Personal data stored in databases and clouds has become a significant risk for customers.
Creating secure payment networks that enable customers to easily make payments without risking the privacy of their data is a critical part of financial data security.
PCI DSS has been designed to address these concerns by introducing rules to protect bank and credit card information.
So what is PCI DSS?
The Payment Card Industry Data Security Standard (PCI DSS) has been created in 2006 as a joint venture of the five largest payment systems brands (Visa, MasterCard, American Express, Discover, and JCB). A set of policies and procedures aimed at optimizing the security of all personal data and information for the processing, transmission, and storage of credit card, cash card, and bank information and also protecting cardholders against misuse of their personal information were introduced. Created and overseen by the independent agency, the Security Standards Council (PCI SSC) PCI DSS’s purpose is to establish an open set of standards to protect consumer information, improve the security of payment card transactions, and reduce credit card fraud.
Why is PCI DSS Certification Important?
It applies to any organization that deals with credit, debit or cash card information, regardless of size and industry.
A data breach that exposes customers’ personal information has serious repercussions for an organization. A breach results in large fines for organizations, years of litigation, declining sales, and most importantly, a badly damaged image.
After experiencing a breach, a business is forced to suspend credit card transactions or pay higher than the initial cost of security compliance.
Advantages of Being PCI DSS Compliant
- Protects the customer’s card data and reduces the risk of data breaches.
- Helps you detect and prevent both physical and network-based attacks.
- Increases customer confidence by using card payments for payments.
- Provides a security standard for you to follow.
- Increases operational efficiency.
- Reduces the cost of data breach.
- Protects your reputation against the loss of trust you will experience in the event of a data breach.
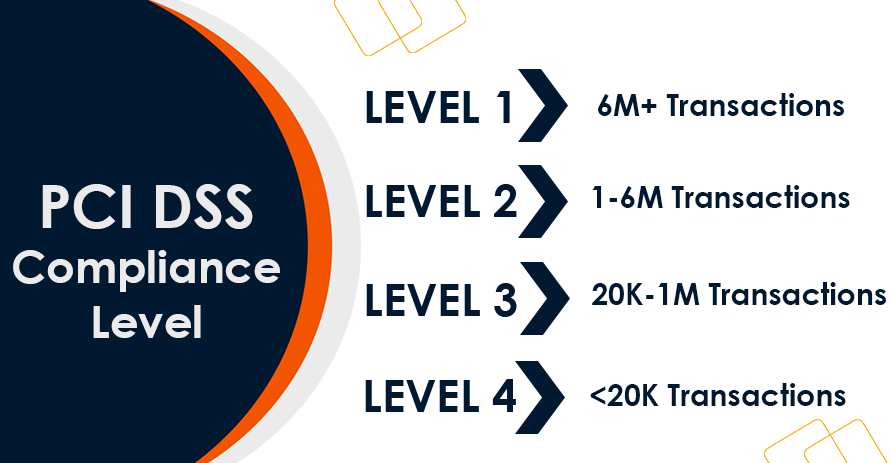
PCI DSS Compliance Levels
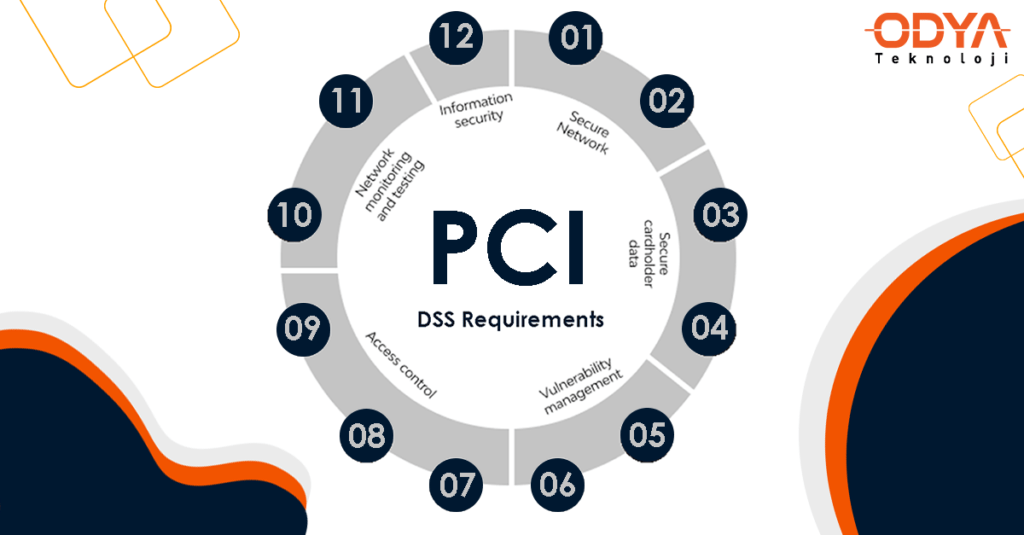
12 Requirements of PCI DSS
PCI SSC identifies 12 requirements for processing cardholder data and maintaining a secure network. It defines the 6 main objectives and sub-headings and the procedures necessary for a business to align.
Secure Network
1. Install and maintain a firewall configuration to protect cardholder data.
2. Don't use vendor-supplied defaults for system passwords and other security parameters.
With Network Configuration Manager, users can easily make bulk changes to network device configurations, including system passwords and security parameters.
Secure cardholder data
3. Protect stored cardholder data.
4. Encrypt transmission of cardholder data across open, public networks.
Cardholder sensitive data and authentication information must be encrypted in transit over open, public networks.
Security vulnerability management
5. Use and regularly update antivirus software.
6. Develop and maintain secure systems and applications.
Access Control
7. Restrict access to cardholder data by business need to know.
The principle of least privilege must be applied when deciding who has access, according to PCI DSS. That idea restricts access to data to only those who require it and only for as long as they require it. Access ought to be determined by a person’s obligations and informational needs.
8. Assign a unique ID to each person with computer access.
9. Restrict physical access to cardholder data.
Network monitoring and testing
10. Track and monitor all access to network resources and cardholder data.
11. Regularly test security systems and processes.
SolarWinds offers both cloud (SolarWinds Threat Monitor) and on-premises (SolarWinds Log & Event Manager) SIEM tools to monitor your network and help protect against potential cybersecurity incidents. Both include near real-time event correlation, automatic threat remediation, and advanced search and forensic analysis.
Information Security
12. Maintain a policy that addresses information security.
A strong PCI DSS compliant security policy helps secure your infrastructure covered by PCI DSS and sets a standard for what is expected of your employees.
It is critical to ensure that every employee understands what is expected of them regarding the security of sensitive customer data. All personnel should be aware of the sensitivity of data and their individual and group responsibilities for protection
SolarWinds Tools Supporting PCI DSS Compliance
Network Configuration Manager
- Network Automation
- Network Compatibility
- Network configuration management
- Security Vulnerability Assessment
- Network insights for Cisco ASA and Cisco Nexus
- Integration with Network Performance Monitor
Access Right Manager
- Monitoring Active Directory
- Windows File Sharing Control
- Monitoring Microsoft Exchange
- SharePoint access monitoring and management
- User provisioning and management
- User permissions analysis
Threat Monitor
- Continuously updated threat Intelligence
- Security Information and Event Manager (SIEM)
- Log Correlation
- Log Event Archive
- Network and Host Intrusion Detection System
- Highly Indexed Log Search Capabilities
Log & Event Manager
- Integration with compliance reporting tools
- Event-time correlation of security events
- Automatic threat optimization
- Advanced search and forensic analysis
- File integrity monitoring
- USB device monitoring
Patch Manager
- Microsoft WSUS patch management
- Integrations with SCCM
- Vulnerability management
- Prebuilt/tested packages
- Patch compatibility reports
- Patch status dashboard
Security Event Manager
- Central log collection and normalization
- Automatic threat detection and response
- Integrated compliance reporting tools
- Intuitive control panel and user interface
- Built-in file integrity monitoring
Server Configuration Monitor
- Basic server and application configurations on Windows and Linux
- Real-time alarming and reporting in case of deviations from the set level
- See who made configuration changes on servers or apps
- Comparing current configurations with previous versions
- Linking configuration changes to performance metrics
- Monitoring server hardware and software inventory
Share this blog post on social media!
Contact us for more information about PCI DSS Regulation!


