Everything You Need To Know About Application Dependency Mapping (ADM)!
Knowing all the inventories is no longer enough in today’s fast-paced IT world. Traditionally, businesses had relatively simple infrastructures; however, most companies today operate in a complex environment with multi or hybrid cloud, hypervisors (VMware, Hyper-V etc.), container systems and micro-services. This makes visibility more difficult than ever before. To maintain the efficiency of your IT environment, your business must have a view of all server hardware, software applications including versions, certificates, patch levels, virtualization and cloud technologies. At the same time, you should be able to see how fast these devices and applications can connect and communicate with each other, and have information about how one change affects the other. At this point, Application Dependency Mapping (ADM) or Network Discovery Tools come into play!
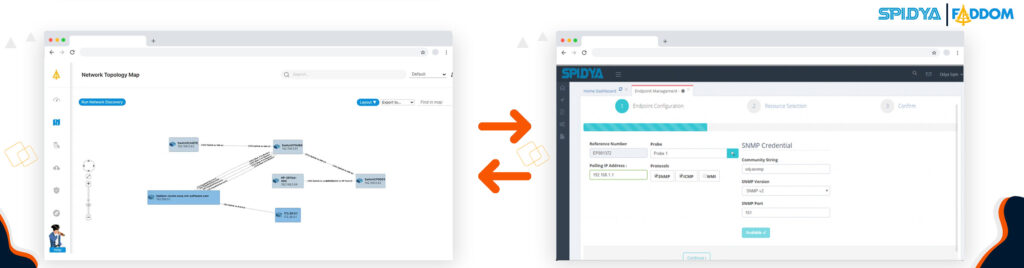
This technology can identify and map all instances, communication channels, applications, as well as ports and services used in your IT ecosystem. Best solutions can also quickly and easily identify VPCs, Subnets and Security Groups on Cloud Providers (eg AWS, Azure and GPS).
When viewed on an intuitive map, you have a visual of your app dependencies that can be shared, drilled deeper, or used for planning and troubleshooting. You can use this image for real-time critical alarms and information that you prioritize in your business strategy, adjustments based on your business context.
Why Are Dependencies Important?
It’s important to know what you have in your ecosystem, but more importantly to acknowledge the impact all your servers and applications have on one another. If you don’t see the cohesion between your applications, it’s hard to predict the impact of changes or pinpoint the root cause of problems. When it comes to use cases such as change impact analysis, application dependencies must be available.
Getting the most out of network or application discovery means having a clear visual of all dependencies on the network. It can be displayed with an easy-to-read color scheme.
Sharing Data with a CMDB
Today your company uses a Configuration Management Database, but you are looking for ways to get more out of the system. Integration with the right application mapping tool can add valuable data to your existing inventory. While a CMDB is a basic repository of knowledge about what you have, adding insights into dependencies and communications can take it to the next level. Out-of-the-box integration with a CMDB such as SPIDYA IT Service Management can provide a single source of reference for all your assets.
Understanding how they communicate and depend on each other streamlines operations, strengthens collaborations, and reduces human error. As always, the best suppliers will adapt to the integrations. So you can maintain the flexibility you need even if your CMDB changes.
Agent or Agentless?
Many application mapping solutions use agents for discovery and prefer it because of better accuracy or affordability, but agents are a cumbersome and complex solution when it comes to discovery.
- First, you need to place agents everywhere, otherwise you risk having gaps in your map and losing comprehensive visibility.
- Second, using agents means you need to know in advance what you’re watching. Because they rely on human knowledge, it makes agent-based solutions less reliable than alternatives.
- Finally, agents may cost less than bundle parts and other hardware, but there are other options on the market.
On the contrary, the use of traffic data is more accurate and lightweight discovery method. It speeds up both the deployment process and time to value. Network traffic is identified in real time, giving instant insight into dependencies and changes. This data is also independent of pre-existing developer designs or network plans, so unexpected connections and dependencies can be found even if they are more than one hop away. Network discovery using traffic data is also much more transparent in terms of cost and maintenance, without requiring any hardware or agents.
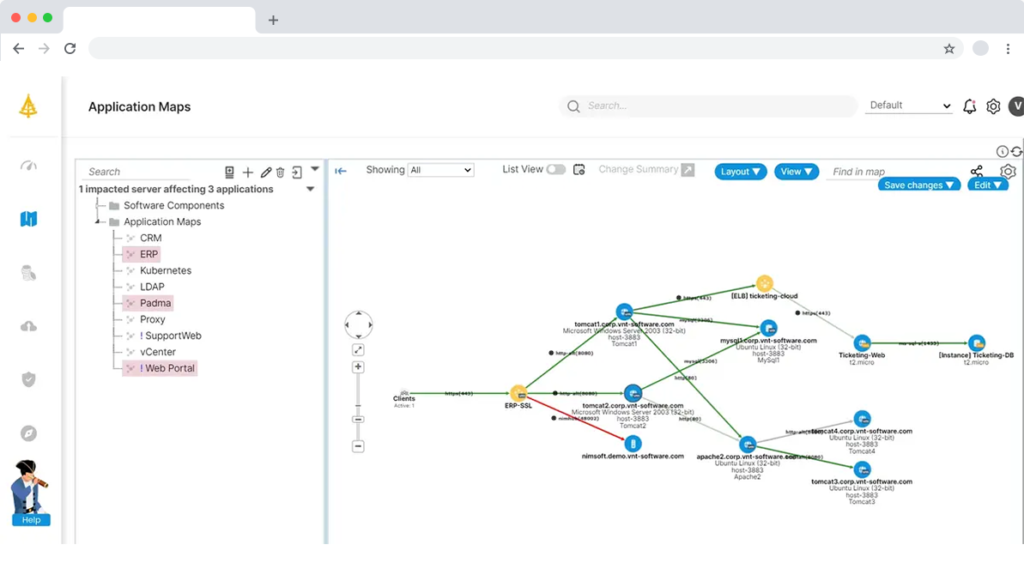
What you gain with Application Dependency Mapping (ADM) is visibility. Therefore, visibility is a fundamental step for use cases by schemes.
The advantages it provides to IT teams
IT Asset Management and Documentation
Discovering the servers and applications you own, as well as dependencies and communications; provides an understanding of the definitions of subnets, VPCs, and security groups in AWS.
By understanding the connections and getting an accurate map, you can retire or merge assets with peace of mind about the business impact that follows.
Data Center Transformation and Migration to the Cloud
Allows you to prioritize asset needs by recognizing their space in your entire ecosystem. From single application retirement to full cloud migrations, you can use your map as a basis for planning and implementing change across operations of any size, revealing the relevance of each asset in relation to business critical systems and services.
Disaster Recovery and Business Continuity
You can identify points of failure for any problem in your environment and quickly isolate the smartest path to recovery. Your map shows you the context for failed connections, bottlenecks, service interruptions, as well as systems that need further investigation.
Micro-segmentation and Cybersecurity
Find applications, servers, and systems that will be affected in the event of a breach or outage, and predetermine the intelligent security policies that handle these events. This prevents you from leaving incident response to chance in the event of a cyberattack.
Contact us for Application Dependency Maps and Network Discovery Solutions!


